$CrowdStrike Holdings, Inc.(CRWD)$
There’s no stopping when it comes to scaling your business, so why should your security remain stagnant? With your organization constantly expanding and your IT and security stack increasing in tools, your threat landscape is bound to grow with it. And by leveraging an increasing number of external applications and software-as-a-service (SaaS)-delivered solutions, you’re broadening your attack surface for new threats to take hold. To ensure full coverage that scales with your business, your security and IT teams need to extend visibility into your application environment and implement effective response controls before an adversary can do serious damage like moving laterally and injecting malware.
CrowdStrike and its CrowdStrike Store partners DoControl and TrueFort help deliver comprehensive SaaS and application security, leveraging the CrowdStrike Falcon® platform’s single, intelligent agent and rich contextual data. The CrowdStrike Store extends the power of the Falcon platform to ensure you can stay ahead of modern attackers — DoControl’s new automated SaaS security app and the Zero Trust capabilities of TrueFort’s existing Fortress application help you to stop threats in your application environment at scale.
Remediate Compromised Assets Hidden in Your SaaS Apps
With many enterprises using SaaS applications daily — like Box, Google Drive, Slack and more — across all functions of the business, your critical corporate data is left outside your security perimeter and relies on the security measures of each SaaS application independently. With increased collaboration in these applications from vendors, partners and customers, controlling data access in an efficient and effective manner is key to ensure complete coverage while minimizing the likelihood of a data breach.
By combining the Falcon platform’s rich telemetry with further visibility and control of SaaS applications on unmanaged devices where Falcon is not present, end users and external collaborators are prevented from uploading, accessing and sharing malicious assets on any of your corporate SaaS applications, ensuring that your employees and external collaborators are protected from malware and advanced threats. To achieve complete control over this growing attack surface, DoControl and CrowdStrike have partnered to help you identify and control the SaaS applications in your environment to achieve speed and agility of response.
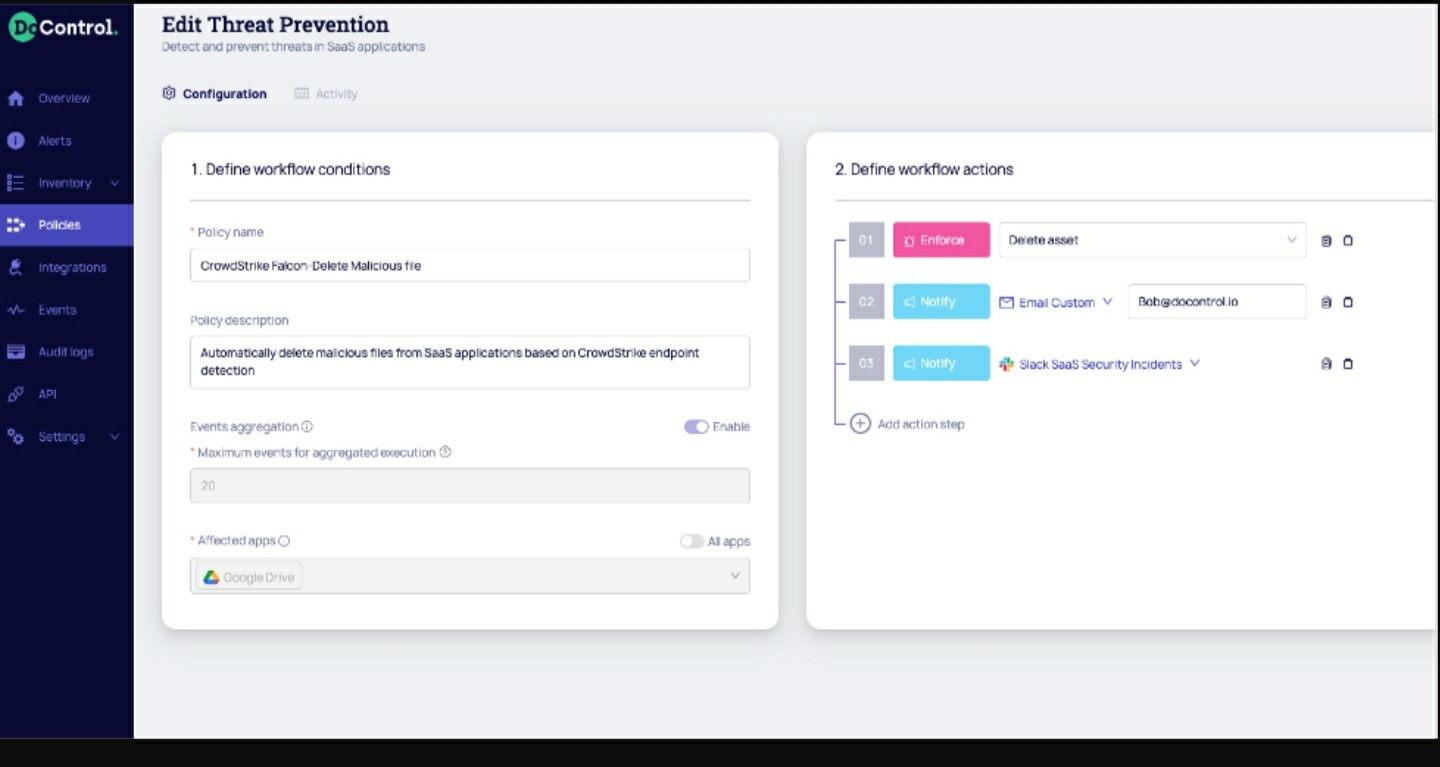
(Click to enlarge)
DoControl automatically cross-references CrowdStrike Falcon detections with the same files stored in your SaaS applications to identify and remediate malicious activity at speed and scale. By immediately alerting your security teams to said cross-referenced detections, workflows can be triggered to remediate hosts by killing processes and file executions and deleting the files. With DoControl and CrowdStrike, you can prevent files from being added, stored or accessed by employees or external collaborators with known compromises, allowing you to gain control over your SaaS applications with faster and more accurate identification and response. By combining DoControl with CrowdStrike Falcon’s rich endpoint telemetry, you can easily manage assets, improve visibility and automate workflows to prevent data breaches in corporate SaaS applications.
Gain Zero Trust Application Protection
Applications and workloads are top breach targets and avenues for adversaries to move laterally in your network. To proactively protect your organization from attacks, you need to fully understand application behavior and reduce excessive trust to effectively block or contain threats like ransomware, insider threats, supply chain attacks and other cyberattacks. TrueFort Fortress has enhanced its existing Zero Trust application protection capabilities with CrowdStrike Falcon to deliver micro-segmentation for all of your applications and workloads.
The TrueFort Fortress app in the CrowdStrike Store leverages the Falcon platform’s rich endpoint data alongside its firewall creation, management and enforcement capabilities to help you gain visibility and control for detection and response at the application level. The Fortress app allows you to visualize your application flows and dependencies, automatically generate policies based on observed behavior, monitor for anomalies, streamline investigations, enable automated policy enforcement, and deliver robust reports — reducing excessive trust and related risks. By using application behavior telemetry from the Falcon platform, machine intelligence, and automation, Fortress continuously assesses and learns each application’s trusted runtime behaviors and creates a dynamic application trust graph, giving you comprehensive visibility. With this Zero Trust baseline for authorized behavior, your team is empowered to continuously identify and remediate risk-related deviations across all of your cloud, hybrid, containerized and on-premises workloads. With TrueFort and CrowdStrike, you can automate adaptive application security to stop threats, reduce your attack surface and stay compliant.
Learn more about how to use TrueFort and CrowdStrike for micro-segmentation in our joint webcast, Stop Cyberthreats with Microsegmentation, on Sep 15, 2021.
Your Business Is Growing — So Should Your Security
With your business growth and increased scale, you need to focus on securing your environment end-to-end with unified platform-delivered solutions that can give you holistic visibility and control to stop breaches. With powerful application and SaaS security delivered by TrueFort and DoControl — available in the CrowdStrike Store — your team can automate detection and response in your complex application environment with proactive and effective tools to prevent malicious activity, stop advanced threats and maintain a high level of security efficacy.
Disclaimer: Investing carries risk. This is not financial advice. The above content should not be regarded as an offer, recommendation, or solicitation on acquiring or disposing of any financial products, any associated discussions, comments, or posts by author or other users should not be considered as such either. It is solely for general information purpose only, which does not consider your own investment objectives, financial situations or needs. TTM assumes no responsibility or warranty for the accuracy and completeness of the information, investors should do their own research and may seek professional advice before investing.
- alexteoh90·2021-09-15????????????????????????????????????????????????????????????????????????????????????????????????????LikeReport
- alexteoh90·2021-09-1512LikeReport
- alexteoh90·2021-09-1515LikeReport
- alexteoh90·2021-09-1514LikeReport
- alexteoh90·2021-09-1513LikeReport
- alexteoh90·2021-09-1510LikeReport
- alexteoh90·2021-09-1511LikeReport
- alexteoh90·2021-09-15aLikeReport
- alexteoh90·2021-09-15bLikeReport
- alexteoh90·2021-09-15cLikeReport
- alexteoh90·2021-09-15dLikeReport
- alexteoh90·2021-09-15?LikeReport
- alexteoh90·2021-09-15eLikeReport
- alexteoh90·2021-09-15fLikeReport
- alexteoh90·2021-09-15gLikeReport